On Cross-cultural Information Security Behaviors in the Workplace
Story of Successful Internet Access in Bulgaria
by Dr. Bobby Swar (Concordia University of Edmonton, Canada) and Dr. Tahir Hameed (SolBridge International School of Business, South Korea
IEEE Internet Initiative eNewsletter, January 2017
Information technology and systems generally bring large benefits to organizations in terms of efficiency, productivity and strategic positioning. They are also the largest source of information-related threats and vulnerabilities. Frequent headlines on data breaches and system compromises highlight the losses of businesses in tune of millions of dollars, delayed services, inconvenience and frustration faced by both the customers and their employees. It is no wonder that information security has evolved into a major discipline in parallel to the advent of information technologies, ubiquitous systems and emerging platforms like Internet of Things (IoT), and cloud. Information assurance, which has become cornerstone of organizational IT strategy, involves identification of critical information assets, deployment resources, authorization and access, identification of threats and vulnerabilities, responses to threats, responsibilities and accountability, damage and disaster recovery, etc.
Organizations take various approaches to prevent and mitigate the information security threats. Technical approach, ranging from basic antivirus installation measures to continuous detection of vulnerabilities in the enterprise software, is the most popular approach among businesses. However, such strategies don’t seem to be enough when nearly half of the intrusions and security violations involve organizational insiders [1]. Insiders (typically employees) who have access to critical information resources are believed to be the weakest link in the information security of organizations [2], although threats from the insiders can be unintentional. While discussing Target’s 40 million customer credit cards data breach in 2013, Upton and Creese (2014) emphasized, “Insiders can do much more serious harm than external hackers, because they have much easier access to systems and a much greater window of opportunity”[3]. Therefore, a second type of information security approach considers individuals, their characteristics, contexts and social interactions, commonly known as behavioral information security.
There is a general agreement that insiders’ behaviors should be monitored and directed to ensure compliance with organizational information security policies. Recent research highlights a need for strategies to alleviate employees’ inappropriate behaviors regarding information systems use, and factors affecting their compliance with information security policies and practices [4-6]. This article looks into information security issues arising from cross-cultural diversity in the workplace.
Interconnection between diverse cultures is almost unavoidable in today’s globalized world. Businesses commonly have offices in multiple countries, employ people from different cultures and outsource software development and back-office functions to far-off locations. Regardless of their work location, people are deeply influenced by cultural values and norms from where they belong. Cultural imperatives lead to different levels of sensitivity towards information security threats. Hence, employees from diverse cultures depict disparate information security behaviors within the same working environment. Several theoretical frameworks have been proposed to look into cross-cultural drivers of such behaviors, for instance Hall’s high-context and low-context cultures [7], Hofstede’s cultural dimensions [8, 9], Trompenaar and Turner’s model of national cultural differences [10] and Koivisto’s cultural crossings [11].
Hofstede’s cultural dimensions, one of the most cited cultural measures at national level, can help discern how national culture relates to an individual’s information security behavior. National culture is generally referred to as the values, beliefs and assumptions learned by an individual while growing up in a particular country. It’s not very difficult to distinguish a person raised in one country from another person from a different country. Hofstede’s explanation comprises five cultural dimensions: individualism vs. collectivism, power distance, uncertainty avoidance, masculinity vs. femininity, and long-term vs. short-term orientation. Intuitively, these cultural dimensions (or individual’s traits) can be employed to better understand and predict an individual’s information security behavior. Consequently, organizations can prepare better strategies to mitigate information security threats and vulnerabilities.
For instance, South Korea and United States were compared on Hofstede’s cultural dimensions in Figure 1 [12], each representing a sample of Asian and Western cultures. South Korea appears to be higher in power distance, collectivist, feminine, uncertainty avoiding, long-term oriented and low indulgence culture in comparison to the U.S.
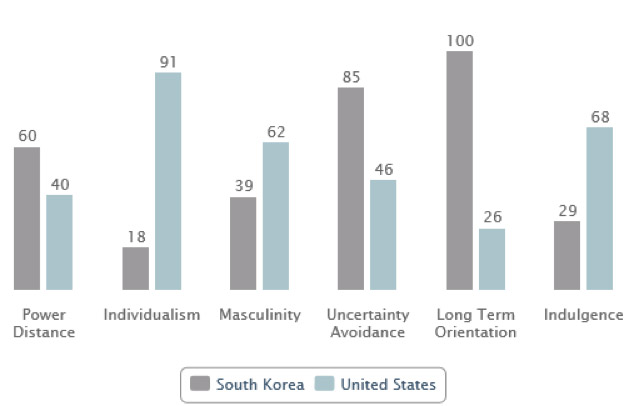
Figure 1. South Korea and United States compared on Hofstede’s cultural dimensions
(Source: https://geert-hofstede.com/countries.html)
Individualism vs. collectivism cultural dimension refers to the extent to which members of a culture tend to have an independent versus inter-dependent construal of the self. In individualistic cultures, the ties between individuals are weak whereas in collectivistic cultures individuals are integrated into strong cohesive groups. Accordingly, trust and privacy become a primary concern in information security. Employees from individualistic cultures may not be ready to trust others in the workplace easily or blindly. As a result, they adopt more preventive information security measures than the employees from collectivistic cultures. For instance, while leaving their computers or authorized devices at the workplace, they conscientiously set-up sleep timers or passwords. They may also be extra cautious in sharing their passwords, protected data or any information with others in the workplace. On the contrary, employees from collectivistic cultures view bonds and relationships as an important aspect of living and working, therefore, they tend to share their computers and passwords with others more freely. They are also more likely to share protected organizational information with closer colleagues. Additional measures like biometrics and radio-frequency identification (RFID) cards reduce the vulnerabilities arising from password-sharing to some extent.
Power distance refers to the inequality of the distribution of power in a country [13]. Cultures with higher power distance are expected to have rigid organizational hierarchies with less openness to new ideas [14] and lower rates of innovation [15]. Individuals coming from higher power distance cultures are more likely to resist new information security policies, regulations and practices. Training and awareness programs have been identified as the most supportive interventions for improvements in information security behaviors. However, quiet intuitively, strong involvement and interest of the top in pushing down the policies should work out faster for the organizations with many employees from higher power distance cultures. That, in turn, would pose another challenge for highly diverse organizations, i.e., to balance the top-down with bottom-up strategies for effective communications and change management.
Another cultural dimension is uncertainty avoidance which refers to the extent to which members of a culture feel threatened by uncertainty or unknown situations. It corresponds to a higher level of perceived significance to follow the norms, rules and standards [16], hence risk-aversion. Intuitively speaking, such employees are more likely to adhere to information security rules and regulations set by their organizations and vice versa. Therefore, organizations with larger number of employees from uncertainty avoiding cultures need to clearly define the policies, procedures, definitions of critical information items, and ownership of those items. This dimension could be considered along with power-distance dimension while designing information security behavior strategies.
Talking about the masculinity-femininity cultural dimension, people are usually task oriented in a masculine culture [17]. They are characterized by competition, ambition and focus on performance and material values [7]. Contrarily, people are relationship-oriented and are characterized by solidarity, consensus-seeking and concern about social relationships [10] in feminine cultures. Employees from the masculine culture are more vulnerable to misuse information resources for personal gains. It means there could be higher threats from disgruntled employees hailing from the masculine cultures than those from the feminine cultures. Correspondingly, national laws and norms in countries with masculine cultures might be more supportive to organizations in dealing with such threats and their aftermath. Therefore, an organization’s location in a nation pre-dominantly with masculine or feminine culture would also underpin the design of its information security strategies.
Long-term vs. short-term orientation dimension is concerned with time orientation in cultures. Long-term oriented persons look for future rewards, frequently sacrificing immediate gains. On the other hand, members from short-term orientation cultures have virtues related to the past and present, especially respect for tradition, preservation of ‘face’ and fulfilling social obligations [6]. Employees from short-term oriented cultures tend to comply relatively less with information security policies and are more likely to be careless with critical information items and resources. On the contrary, employees from feminine cultures are usually long-term oriented, and they might like career-progression and trust which comes with higher levels of access to information and responsibility. It implies both time-orientation and masculinity should be considered together when developing information security strategies.
In sum, given the fact that threats to organizational information assets are increasing, it is critical to understand how cross-cultural issues could affect information security behaviors of employees in the workplace. In addition to the technical and strategic information security requirements, Chief Information Officers (CIOs) and Chief Information Security Officers (CISOs) should strive to understand the composition of their organizations and the cultures of their employees in order to develop appropriate information security strategies, training and communications programs, incentives and penalties, and protective clauses in their contracts. Rather than protecting organizational information assets from external threats only, they should rightly identify and foster an organizational information (security) culture which embraces cross-cultural issues arising from diversity. That would help mitigate internal information security threats.
References:
[1] R. E. Crossler et al., “Future directions for behavioral information security research,” computers & security, vol. 32, pp. 90-101, 2013.
[2] J. L. Spears, and H. Barki, “User participation in information systems security risk management,” MIS quarterly, pp. 503-522, 2010.
[3] D. M. Upton, and S. Creese, “The danger from within,” Harvard business review, vol. 92, no. 9, pp. 94-101, 2014.
[4] B. Bulgurcu, H. Cavusoglu, and I. Benbasat, “Information security policy compliance: an empirical study of rationality-based beliefs and information security awareness,” MIS quarterly, vol. 34, no. 3, pp. 523-548, 2010.
[5] A. C. Johnston, and M. Warkentin, “Fear appeals and information security behaviors: an empirical study,” MIS quarterly, pp. 549-566, 2010.
[6] Q. Hu et al., “Managing employee compliance with information security policies: The critical role of top management and organizational culture,” Decision Sciences, vol. 43, no. 4, pp. 615-660, 2012.
[7] E. T. Hall, “The hidden dimension,” 1966.
[8] G. H. Hofstede, and G. Hofstede, Culture's consequences: Comparing values, behaviors, institutions and organizations across nations: Sage, 2001.
[9] G. Hofstede, Culture's consequences: International differences in work-related values: sage, 1984.
[10] F. Trompenaars, and C. Hampden-Turner, Riding the waves of culture: Understanding diversity in global business: Nicholas Brealey Publishing, 2011.
[11] J. V. Koivisto, and M. Lampinen, Crossing National and Corporate Cultures: In-depth Analysis of the Cross-cultural Organisation in the Integration of a Finnish Firm's Acquisition Case in Hong Kong: Helsinki School of Economics and Business Administration, 2001.
[12] G. Hofstede. 25 November, 2016; https://geert-hofstede.com/countries.html.
[13] A. A. Erumban, and S. B. De Jong, “Cross-country differences in ICT adoption: A consequence of Culture?,” Journal of World Business, vol. 41, no. 4, pp. 302-314, 2006.
[14] M. D. Mumford, and B. Licuanan, “Leading for innovation: Conclusions, issues, and directions,” The leadership quarterly, vol. 15, no. 1, pp. 163-171, 2004.
[15] R. W. Zmud, “Diffusion of modern software practices: influence of centralization and formalization,” Management science, vol. 28, no. 12, pp. 1421-1431, 1982.
[16] P. A. Pavlou, and L. Chai, “What Drives Electronic Commerce across Cultures? Across-Cultural Empirical Investigation of the Theory of Planned Behavior,” J. Electron. Commerce Res., vol. 3, no. 4, pp. 240-253, 2002.
[17] D. Gefen, and D. W. Straub, “Gender differences in the perception and use of e-mail: An extension to the technology acceptance model,” MIS quarterly, pp. 389-400, 1997.
 Bobby Swar
Bobby Swar
Bobby Swar is an Assistant Professor at Concordia University of Edmonton in Canada. He received his Ph.D. in Information and Telecommunication Technology Management from KAIST. His research interests include IT outsourcing, health informatics, social media and information security and assurance management. He has published articles in journals like Information Systems Frontier, Social Science Computer Review, Innovation: Management, Policy & Practice, Scientometrics, Information Development, Journal of the American Society for Information Science and Technology (JASIST), Journal of Information Technology Teaching cases and Int. J. Services Technology and Management. He can be reached at bobby.swar@concordia.ab.ca
 Dr. Tahir Hameed
Dr. Tahir Hameed
Dr. Tahir Hameed has been associated with SolBridge International School of Business in South Korea since 2012. He teaches courses related to information systems and technology management at the masters and bachelors levels. Prior to joining SolBridge, Dr. Hameed obtained his Ph.D. in Information Technology Management from the Korea Advanced Institute of Science and Technology (KAIST), and obtained his Masters in Computer Science from Lahore University of Management Sciences (LUMS). His research interests include the areas of information technology standards, innovation, IT policy, information systems adoption, and knowledge management. He has published extensively in prestigious journals such as Telecommunications Policy, Technological Forecasting and Social Change, World Development, and Journal of Knowledge Management. He has presented several papers at leading conferences including IEEE conference on Industrial Engineering and Engineering Management and Australasian Conference on Information Systems. Dr. Hameed’s current research focus is in the areas of health informatics, knowledge management systems, educational information technology, and technology commercialization. He can be reached at tahir@solbridge.ac.kr.
Editor:
 Ankur Chattopadhyay
Ankur Chattopadhyay
Dr. Ankur Chattopadhyay is an Assistant Professor in the Information and Computing Sciences (ICS) department at the University of Wisconsin, Green Bay. Ankur is a computer scientist plus computer engineer, whose research work is focused on addressing privacy issues in video surveillance. He has a PhD in computer science from the University of Colorado, Colorado Springs. His research interests include computer vision, pattern recognition, security, image processing & analysis and computer science education. He has published and presented in international conferences like ACM SIGCSE, IEEE CVPR and IEEE FIE. Ankur has more than ten years of experience in both academics and industry. As an academician, his passion is teaching computer science, conducting research in security & surveillance and applying his research to improve computer science education. His teaching interests include a wide variety of courses in computer science, especially in the area of security, programming and algorithms. His industry profile includes multiple roles such as IT analyst, software engineer and embedded systems engineer, having worked with Tata Consultancy Services for several years.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.


