Blockchain: A Technical Overview
By Javaid Iqbal Zahid, Dr. Alex Ferworn, Dr. Fatima Hussain
Ryerson University, Department of Computer Science
IEEE Internet Policy Newsletter, March 2018
Discuss this topic on Collabratec:
It can be argued that blockchain technology is the real reason for success of cryptocurrencies. From a technical perspective—independent of Bitcoin or other currencies—blockchain can be applied to many scenarios where transaction verification is a must. In fact, many researchers have already started exploring different avenues where modified versions of blockchain technology can be applied to non-financial transactions. Blockchain is a protocol that uses existing cryptographic techniques to ensure the security and privacy of information, its integrity, and provides a mechanism for the authentication of participating entities. This article reviews various cryptographic algorithms that can be implemented in conjunction with blockchain technology.
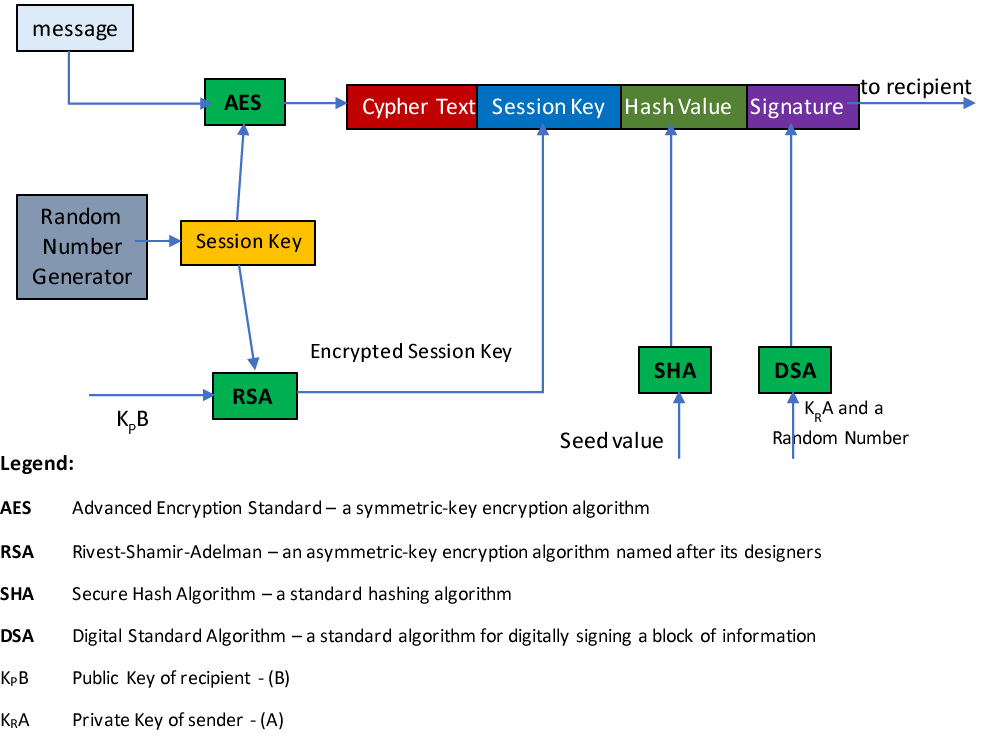
Figure 1: Message Processing using Blockchain
Encryption algorithms provide privacy and security of information against eavesdropping. A symmetric-key algorithm, like AES (Advanced Encryption Standard), is used for encryption that changes the plaintext message (or transaction) into a ciphertext, using a session key either generated by a random number generator or supplied by trusted key infrastructure. Encryption is the only technique that provides privacy and confidentiality of information. However, the session key used for encryption must be conveyed to the recipient through a secure channel. This can be done by encrypting the key with a public-key cryptography algorithm like RSA (Rivest, Shamir, and Adelmen). In RSA, the public key of the recipient is used for encryption, and the recipient uses his or her private key to recover the original session key. The encrypted session key is appended to the ciphertext. The appended ciphertext and session key are presented to a hashing algorithm like the Secure Hash Algorithm (SHA) to obtain hash value—also called a message digest (MD). Essentially, the hash value uniquely identifies the data. The hash value is then appended to the ciphertext and session key block. Hash value is used to ensure that the ciphertext + session key block is not modified or replaced by any “hacker.” The sender signs the entire block by providing his or her signature that is verified by the receiver to ensure sender’s identity. Signature algorithms, like Digital Signature Algorithm (DSA), help in ensuring non-repudiation in case there is a denial of sending or receiving the message in question.
A group, participating in the network, has the choice to select any encryption, hashing, and signature algorithms. There are varieties of these algorithms available for implementation. On the receiver side, all four steps are carried out in reverse order to get to the original plaintext message (or transaction). These four types of algorithms when judicially employed with networking protocols, can provide the most robust scheme of information exchange over a non-secure network like the internet.
Once a block of information is exchanged between two participants and is further chained to subsequent blocks, it can form a secure database of information, thereby simulating the blockchain used in cryptocurrencies. A typical structure of a block and its chain is in Figure 2.
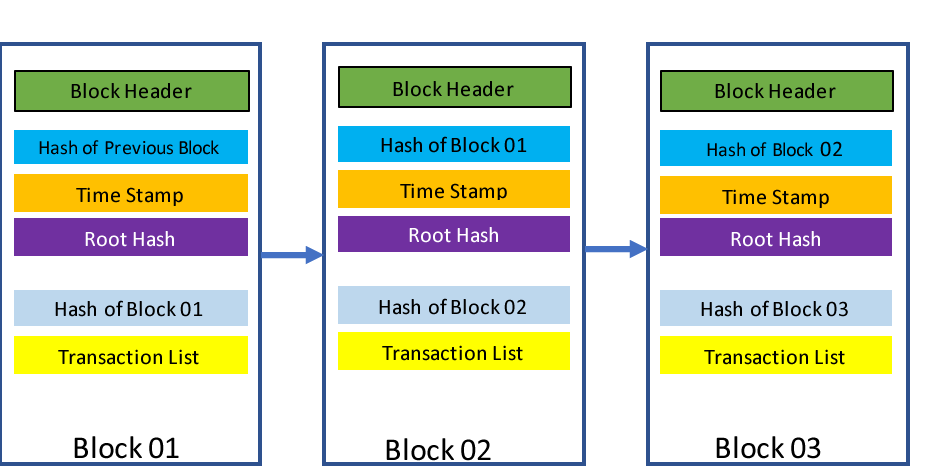
Figure 2: Structure of Information Block
Which security mechanism provides the intended security service is shown in Table 1:
Table 1 : Security Services
|
Intended Security Service |
Security Mechanism |
|
Confidentiality |
Encryption |
|
Privacy |
Encryption |
|
Information Integrity |
Message Digest Algorithm or Hashing Algorithm |
|
User/Entity Authentication |
Digital Signature Algorithm |
|
Non-Repudiation |
Digital Signature Algorithm |
Mining of Blockchain
Each participating node in the network is authorized to generate its own message (transaction) after receiving a message from other nodes. First, it verifies the sender by using the sender’s signature, and checks the hash value of the message. To add own message to the chain, it is required to find a nonce which when hashed with the transaction and hash value of the previous block produces a hash with a certain number of zeros (a Bitcoin requirement). This is called Proof of Work (PoW). This requires extensive computing power. The node that provides PoW can add its message block to the received block adding to the “chain.” For some real-time applications, time delays might not be acceptable. For example, when operating in public safety and disaster recovery situations, timely actions are required upon receipt of critical information.
Verification of Blocks by Consensus
Another equally important aspect of using blockchain technology is verification of added message block, requires due consideration. In Bitcoin, each new block is broadcast on the network. Participants receiving the block, are required to vote for the validity of the message block using an algorithm that would solve problems like the Byzantine General’s Problem (BGP). Once verified by a majority decision, the message block becomes part of the chain. Again, applying such an algorithm takes time and might not be suitable for the time-critical applications mentioned above. Again, this is an area of ongoing research.
Distributed Ledger
In Bitcoin and other cryptocurrencies, transparent distributed ledger comprised of blockchains is maintained, and its copy is held by every network participant. Is there a requirement of distributed or centralized ledger? Can transparency and redundancy be provided by other means? How can Internet of Things (IoT) nodes—that have limited computed power—be employed in smart environments? Researchers are making efforts to find answers to such practical questions.
The Future of Blockchain
Adaption of blockchains in e-Government, smart contracts, IoT, smart grids, smart cities, legal systems, public safety, public health, estate ownerships, property transactions, supply chain management, and many more is being considered rigorously. Many small start-ups are involved in studying applications of blockchain technology. The last decade has seen the growth of Bitcoin, and recently Bitcoin has gained enormous support from investors, thereby, raising its stock value. We believe the next decade will see the application of blockchain in other public and private sectors. This will have a significant enhancement in security and privacy of information.
There are three areas that require attention to make blockchain a viable technology to be used in broader applications. Firstly, the time complexity of various algorithms providing utility services within blockchain schemes must be significantly reduced to allow time-critical transactions to occur; secondly, the implementation of blockchain technology in distributed as well as in centralized computing environments must be possible; and, thirdly, the provision of security and privacy when blockchain technology is employed in open/public networks must be continuously re-addressed.
We believe practical and reliable solutions to the above challenges will expedite the use of blockchain technology and create a new capability within information networks of the future.
References:
[1] Satoshi Nakamato, “Bitcoin: A peer-to-Peer Electronic Cash System.” Available on the internet as a free article.
[2] Nir Kshetri, “Can Blockchain Strengthen the Internet of Things,” IEEE IT Pro, July/Aug. 2017.
[3] William Stallings, “Cryptography and Network Security,” Pearson, 2014.
[4] Konstantinos Christidis et. el., “Blockchains and Smart Contract for the Internet of Things,” IEEE Access, DOI 10.1109/ACCESS.2016.25566399, June 3, 2016.
[5] Jesse YIi-Huumo et. el., “Where is current Research on Blockchain Technology? – A Systematic Review,” PLoS ONE | DOI:10.1371-0163477, Oct. 3, 2016.
 Dr. Fatima Hussain
Dr. Fatima Hussain
Dr. Fatima Hussain is currently working as an Adjunct Professor in Ryerson University, Toronto. Prior to this, she was working as an Assistant Professor in University of Guelph, Canada. Ms. Hussain has done her PhD and MASc. in Electrical & Computer Engineering from Ryerson University. She is engaged in various NCSER funded industrial projects such as; Smart Machine Automation, Smart Warehouse, Smart Watch etc. Dr. Hussain has more than 8 years of teaching/ research experience in GTA and overseas. Her research interests include Machine Learning, Internet of Things Networks, and Public Safety. She has dozens of journals and conference papers and an introductory book on "Internet of Things; Building Blocks and Business Models", on her credit. She is serving as an editor and technical lead for IEEE WIE Newsletter, Toronto section.

Dr. Ferworn is a Professor of Computer Science in the Faculty of Science at Ryerson University. Alex has a broad range of research interests related to Computational Public Safety. His award-winning work has been widely publicized in the media. In 2013 he was named the EURAXESS Canadian “Science Slam” champion for his ability to communicate complex ideas to a general audience in compelling ways. “Partners in Research” named him the Canadian “Technology Ambassador” for 2014 for his body of work and his outreach activities.
Javaid Iqbal Zahid
Javaid Iqbal Zahid received his Bachelor of Science in Telecommunication Engineering and Master of Science in Electrical Engineering degree both from University of Engineering and Technology, Lahore, Pakistan. He has over 25 years of experience as in academics and research. He specializes in Signal Processing, Information Theory, Wireless Communication, Information Security, and Analysis of Algorithms. Currently, he is part of Network Centric Applied Research Team (NCART) at Department of Computer Science, Ryerson University, Toronto, Canada. Mr. Javaid is member of IEEE Computer Society, IEEE Communication Society, IEEE Information Theory Society, and Internet Society.
Editor:
 Dr. Syed Hassan Ahmed
Dr. Syed Hassan Ahmed
Syed Hassan Ahmed completed his B.S in Computer Science from Kohat University of Science & Technology (KUST), Pakistan and Masters combined Ph.D. Degree from School of Computer Science and Engineering (SCSE), Kyungpook National University (KNU), Republic of Korea. In summer 2015, he was also a visiting researcher at the Georgia Tech, Atlanta, USA. Collectively, Dr. Hassan authored/co-authored over 100 international publications including Journal articles, Conference Proceedings, Book Chapters, and 02 books. From the year 2014 to 2016, he consequently won the Research Contribution awards by SCSE at KNU, Korea. In 2016, his work on robust content retrieval in future vehicular networks lead him to win the Qualcomm Innovation Award at KNU, Korea. Currently, Dr. Hassan is a Post-Doctoral Fellow in the Department of Electrical and Computer Engineering, University of Central Florida, Orlando, FL, USA. His research interests include Sensor and Ad hoc Networks, Cyber-Physical Systems, Vehicular Communications and Future Internet. Dr. Hassan is an IEEE and ACM member, serving as a TPC Member or Reviewer in 60+ International Conferences and Workshops including IEEE Globecom, IEEE ICC, IEEE CCNC, IEEE ICNC, IEEE VTC, IEEE INFOCOM, ACM CoNEXT, ACM SAC, and much more. Furthermore, he has been reviewing papers for 30+ International Journals including IEEE Wireless Communications Magazine, IEEE Networks Magazine, IEEE Communications Magazine, IEEE Communications Letters, IEEE Sensors Letters, IEEE Transactions on Industrial Informatics | Vehicular Technologies | Intelligent Transportation Systems | Big Data | Mobile Computing, Elsevier Computer Communications, and Computer Networks.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.



