Integration of Internet of Things (IoT) and Cloud Computing: Privacy Concerns and Possible Solutions
Homomorphic cryptography to address privacy concerns
By Abdulatif Alabdulatif, Ibrahim Khalil, and Syed Hassan Ahmed
IEEE Internet Policy Newsletter, September 2018
Discuss this topic on Collabratec:
The rapid growth of the Internet of Things (IoT) technologies is revolutionizing how communities live and interact by enabling IoT devices (e.g., mobiles, sensors) to work as interconnected systems of digital and personal information. Smart grid and power systems, e-health and assisted living systems, and industrial and environmental monitoring are the major application areas that stand to gain from the growth of IoT.
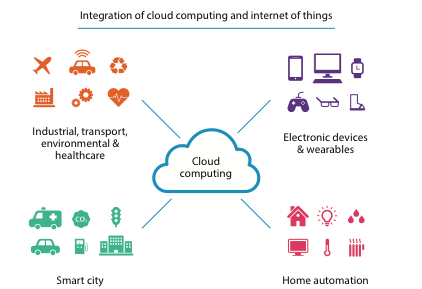
By 2020, it is estimated there will be about 20 billion IoT connected devices in the world[6]. This increase in the number of IoT-enabled devices brings with it increased privacy concerns. In such systems, tremendous amounts of sensitive data are generated, stored and processed—and it is becoming more complex and challenging to protect such data. Cloud computing has massive resources and can play a vital role in the storage and management of IoT data. It can provide real-time IoT-based services in a distributed and effective manner. Figure 1 shows various IoT-based applications that can take advantage of integration with cloud computing.
However, cloud computing is considered a public and unsecured platform, which makes it exposed to various malicious activities from both outside and within the cloud platform. Therefore, comprehensive privacy solutions are critical to ensure the successful integration between cloud computing and IoT-based applications. This is essential to not only protect the privacy of IoT data but also to develop privacy-preserving analytical services models for cloud-assisted IoT applications.
Figure 1: An overview of IoT applications domains that can benefit from data analytics model in cloud computing.
One of the most promising solutions to address the privacy issues in cloud-integrated IoT applications is a cryptographic approach. There are two main categories of this approach, which are traditional cryptography and homomorphic-based cryptography. Traditional cryptography offers a convenient solution for ensuring the privacy of outsourced IoT data in the cloud. Although the risk of sensitive information leakage is significantly reduced by adapting traditional cryptographic techniques, it is not an ideal solution for cloud-integrated IoT applications that require real-time, responsive analytical services. This is because of the limited capabilities of traditional cryptography, which does not support any computations capabilities in an encrypted domain. To develop comprehensive privacy-preserving IoT solutions in the cloud, secure data auditing and managing is essential, along with the ability to perform analytical services which take full advantage of the cloud computing platform. Hence, traditional cryptography is not widely applied in cloud computing due to capabilities shortages in relation to auditing and processing data, key management for access control, and the additional computation and communication costs.
Homomorphic-based cryptography, which has the ability to perform computations on encrypted data, overcomes traditional cryptography limitations and is the superior approach. Rivest et al. introduced the first homomorphic-based cryptography technique in the late 1970s[4]. Since that time several homomorphic cryptosystems (known as Partially Homomorphic Encryption (PHE)) techniques have been developed. However, they are support limited computation capabilities. In 2009, Craig Gentry developed the first Fully Homomorphic Encryption (FHE) cryptosystem[1] that had the ability to evaluate any mathematical function in an encrypted domain. But Gentry’s FHE cryptosystem was impractical for real-world applications, due to the massive overheads associated with its computations. Gentry himself estimated a simple encrypted Google search that would take about a trillion times longer compared to a typical unencrypted search. Several FHE implementations have been created using already existing libraries to simplify FHE operations. The three most prominent efforts are the FHEW[4] and Microsoft’s SEAL [2]. HElib has a special tuning code to enhance performance and also offers the richest API of the three libraries. It speeds up homomorphic Advanced Encryption Standard (AES) scheme performance from 36 to 3 hours[3]. Furthermore, HElib algorithms have a variety of mathematical capabilities that have the advantage over other FHE schemes.
Homomorphic-based techniques have been proven to support a high level of protection for sensitive data. As previously mentioned, homomorphic-based encrypted data are processed in an encrypted domain without the need to be decrypted. This is considered to be the main difference between the two cryptographic. Data is secured through encryption from its sources (e.g., IoT sensors) upon being sent through the network to cloud computing. The encrypted data is then stored in the cloud for further processing in an encrypted domain. Later, the data owner can retrieve and decrypt the evaluation results on the secure side. This process not only eliminates the need to interact with Trusted Third Parties (TTPs) to manage and process the data, it also significantly reduces the massive communication overhead and eliminates the need for encryption/decryption keys, which are major obstacles in traditional cryptography techniques.
In the future, a major focus will be on developing HE cryptosystems that improve both performance and computations capabilities. These efforts will play a major role in the integration of cloud computing and IoT paradigms. Successful delegation of the privacy-preserving process to massive cloud resources will widen the applicability of cloud-integrated IoT applications that require both real-time IoT-cloud-based analytic services and a high level of data privacy. A number of sectors stand to benefit from such advances, particularly the industrial, smart grid, and healthcare sectors.
References:
[1] C. Gentry, “Fully homomorphic encryption using ideal lattices,” In Proceedings of the 41st Annual ACM Symposium on Theory of Computing, STOC 2009, Bethesda, MD, USA, May 31 - June 2, 2009, pages 169–178, 2009.
[2] H. Chen, K. Laine, R. Player, Simple encrypted arithmetic library - SEAL v2.1, IACR Cryptology ePrint Archive 2017 (2017) 224.
[3] I. Gvero. Cloud computing concepts, technology and architecture by Thomas Erl, Zaigham Mahmood and Ricardo Puttini. ACM SIGSOFT Software Engineering Notes, 39(4):37–38, 2014.
[4] R. L. Rivest, L. Adleman, and M. L. Dertouzos. On data banks and privacy homomorphisms. Foundations of secure computation, 4(11):169–180, 1978.
[5] L. Ducas, D. Micciancio, FHEW: Bootstrapping homomorphic encryption in less than a second, in: Advances in Cryptology - EUROCRYPT 2015 - 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, April 26-30, 2015, Proceedings, Part I, 2015, pp. 617–640.
[6] R. Van der Meulen, “Gartner Says 6.4 Billion Connected Things Will Be in Use in 2016," https://www.gartner.com/newsroom/id/3165317.
 Abdulatif Alabdulatif
Abdulatif Alabdulatif
Abdulatif Alabdulatif is currently a Ph.D. student School of Computer Science & IT, RMIT University, Melbourne, Australia. He was awarded a B.Sc. degree in Computer Science from Qassim University, Alqassim, Saudi Arabia, in 2008 and a Masters in Computer Science from RMIT University, in 2013. His research interests include applied cryptography, computer and network security and privacy-preserving data mining.
Ibrahim Khalil
Ibrahim Khalil is an Associate Professor in School of Computer Science & IT, RMIT University, Melbourne, Australia. He received the Ph.D. degree from the University of Berne, Switzerland, in 2003. He has several years of experience in Silicon Valley Companies. Ibrahim also worked with EPFL and the University of Berne in Switzerland, and Osaka University in Japan. His research interests include scalable computing in distributed systems, e-health, wireless and body sensor networks, biomedical signal processing, remote health care, network and data security, secure data analytics and privacy.
 Syed Hassan Ahmed
Syed Hassan Ahmed
Syed Hassan Ahmed (S'13, M'17, SM'18) is currently an Assistant Professor in the Computer Science Department of Georgia Southern University (GSU) at Statesboro, USA. Before starting at GSU, Dr. Hassan was a Post-Doctoral Fellow in the Department of Electrical and Computer Engineering, University of Central Florida, Orlando. Previously, he completed his B.S in Computer Science from Kohat University of Science and Technology (KUST), Pakistan and Master combined Ph.D. Degree from School of Computer Science and Engineering (SCSE), Kyungpook National University (KNU), Republic of Korea. In summer 2015, he was a visiting Ph.D. student at the Georgia Tech, Atlanta, USA. Collectively, Dr. Hassan authored/co-authored over 130 international publications including Journal articles, Conference Proceedings, Book Chapters, and 03 books. From the year 2014 to 2016, he consequently won the Research Contribution awards by SCSE at KNU, Korea. In 2016, his work on robust content retrieval in future vehicular networks lead him to win the Qualcomm Innovation Award at KNU, Korea. Dr. Hassan is an active IEEE Senior Member and ACM Professional Member and his research interests include Sensor and Ad hoc Networks, Cyber-Physical Systems, Vehicular Communications and Future Internet.
Editor:
 Dr. Rasheed Hussain
Dr. Rasheed Hussain
Dr. Rasheed Hussain received his B.S. in Computer Software Engineering from N-W.F.P University of Engineering and Technology, Peshawar, Pakistan in 2007, MS and PhD degrees in Computer Engineering from Hanyang University, South Korea, in 2010 and February 2015, respectively. He also worked as a Postdoctoral Research Fellow in Hanyang University South Korea from March 2015 till August 2015. Furthermore, he worked as a Guest researcher in University of Amsterdam (UvA), Netherlands and consultant for Innopolis University, Russia from September 2015 till June 2016. Hussain is currently working as Assistant Professor at Innopolis University, Russia and establishing a new Masters program (Secure System and Network Engineering). He has authored and co-authored more than 45 papers in renowned national and international journals and conferences. He serves as reviewer for many journals from IEEE, Springer, Elsevier, and IET that include IEEE Sensors Journal, IEEE TVT, IEEE T-ITS, IEEE TIE, IEEE Comm. Magazine, Elsevier ADHOC, Elsevier JPDC, Elsevier VehCom, Springer WIRE, Springer JNSM, and many more. He also served as reviewer and/or TPC for renowned international conferences of repute including IEEE INFOCOM, IEEE GLOBECOM, IEEE VTC, IEEE VNC, IEEE ICC, IEEE PCCC, IEEE NoF, and many more.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.



