Integrating Internet of Things and Blockchain: Use Cases
By Javaid Iqbal Zahid, Fatima Hussain and Alexander Ferworn, Department of Computer Science, Ryerson University, Canada
IEEE Internet Initiative eNewsletter, November 2017
Discuss this topic on Collabratec:
Internet of Things
The Internet of Things (IoT) is an interconnected network of smart devices capable of exchanging information while changing their state dynamically and adaptively. IoT capabilities are considered as “game changing” when combined with the concepts of big data analytics and cloud computing.
IoT has brought a new technological revolution across the globe. IoT networks are distributed by nature. This reality has brought in large scale security threats. IoT devices exchange and process massive amounts of data and are exposed to a variety of cyberattacks. Traditional centralized security models have limited utility for IoT applications due to their limitations. Therefore, lightweight, scalable, and distributed security measures are required.
Blockchain
Blockchain is at the heart of Bitcoin, an electronic payment system based on cryptographic proof instead of trust allowing any two willing parties to transact directly with each other without the need for a trusted third party. Cryptographic hash functions and digital signature are the two algorithms employed for ensuring the integrity of transactions and authenticity of the owner of the transaction. As shown in the diagram below, each block of information flows from one owner to the other forming a chain of blocks connected to each other as a verified transaction. An owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. This sequence of action is listed below.
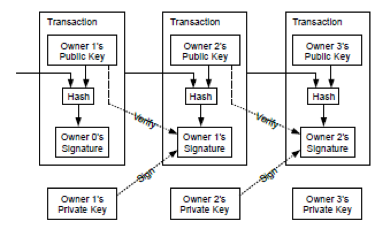
- New transactions are broadcast to all nodes.
- Each node collects new transaction into a block.
- Each node works on finding a difficult proof-of-work (POW) for its block.
- When a node finds a POW, it broadcasts the block to all nodes.
- Nodes accept the block only if transactions in it are valid and not already spent.
- Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
Blockchain becomes part of a distributed ledger, a copy of which is kept by each participant. However, in its current application for Bitcoin, privacy of a transaction is not provided and all transactions are visible to all authorized parties on the Bitcoin network.
Integrating IoT and Blockchain Technology: Case Studies
Blockchain technologies can help in improving the security of IoT applications in healthcare, smart cities, agriculture, energy grids, water management, public safety, supply chain management, education, and similar application areas. Some of the use cases, where blockchain technology can benefit IoT, are discussed below:
A. Public Health – Counterfeit Drugs
The existence of counterfeit drugs is an urgent and acute worldwide problem. According to the World Health Organization, 10 percent of drugs are counterfeit worldwide and in developing countries the amount may be up to 30 percent. Such counterfeiting affects drug supplies related to over-the-counter prescription drugs. In the best case, the counterfeit drug is inert with a user suffering simply from the malady they already have. In the worst case, the counterfeit drugs contain noxious substances placing the user in danger of poisoning. Minimization and control of counterfeit drugs can be achieved by using blockchain and IoT elements. First, each legitimate drug can be physically stamped on location with an identifier that can be entered into a blockchain ledger. Querying copies of the blockchain can be used to determine the authenticity and provide manufacturing details. Forged drugs can be identified and tracked and eliminated from the system.
B. Public Safety – Secure Communication for Critical Incidences
Critical incidents (CIs) are events involving public safety that have the potential to cause major injury or loss of life, societal disruptions, and property damage. Examples of CIs include man-made or natural disasters, such as those caused by the collapse of large buildings, societal violence caused by terrorist activity, or workplace attacks. Various governmental and civil agencies are involved in the response to such events and manage the effects of CIs. Response to CIs usually involves personnel from fire, police, and health services who communicate over networks that record communications. These recordings can be used as evidence by litigants seeking compensation for damages they suffered during the response to the CI. Additionally, CIs invariably include media representation. It is one of the roles of the media to ensure accurate and informative reporting of such events. Essentially, the media act as watchdogs protecting the public interest against malpractice through creating public awareness. It has been proposed that blockchain technology could be used to assist in ensuring that details concerning digital communications occurring and recorded at CIs could be used to encode details of the communications as entries in the distributed leger. This would ensure that all records of communication would be authentic. Access to these records could be obtained through a mechanism like the Bitcoin wallet concept to enable querying the distributed ledger. Thus, the chain of custody of these communications could not be questioned and access to authentic and documented communications could be provided to support media, litigants, and defendants for access to verified facts.
C. Smart City – Smart Homes
In a modern home, a plethora of household devices related to environmental control (sensors), entertainment (TVs, other audio/video equipment), household electronics (refrigerators, dishwashers, electrical lights), and home security systems (surveillance cameras, door locks, alarms) are present. Homeowners or authorized parties can observe and control all the networked IoT devices of a smart home from a remote site. The information from sensors and other devices is sent to a central server or gateway from where it is presented to an enabled controlling device such as a cell phone, tablet, or other computer. Maintaining the security of this information is critical not only from a reliability point of view but also from the point of view of intrusion detection and documentation. Using blockchain the security and privacy of smart home systems can be achieved by recording communication and control information as transactions in the distributed ledger. Confidentiality can be provided by using symmetric cryptography (AES like algorithms), integrity of transaction by hashing functions, and authenticity/non-repudiation by asymmetric cryptography (like RSA/ElGamal like algorithms). With the addition of time-stamping and proper encapsulation, a robust security can be ensured. Any investigation could immediately verify this information and the added benefit of its distributed storage would make it difficult to erase or corrupt. Efforts to disrupt or corrupt the system can be immediately detected. A DOS, DDOS, or man-in-the middle attack can be thwarted with a robust security mechanism. Transactions between nodes and between nodes and cloud can be verified and any unauthorized transaction can be rejected.
D. Software Updates – Software Updating of IoT Edge Nodes
Edge devices in IoT frameworks are devices with low, medium, and high levels of computing power. With increasing system-on-a-chip capabilities, edge devices are becoming more capable and smarter. A small sensor might have to employ the smallest chip having adequate computing power. However, something as large as a refrigerator can be equipped with a much more powerful computing system. If all of the edge devices have some form of computing power their functionality can be reconfigured by sending reconfiguration parameters. Such devices can form peer-to-peer networks without involving cloud computing resources. These devices can share IoT service functions by communicating directly with each other. Device parameters related to functionality and device management can be downloaded or updated periodically or on-demand. This scenario can be achieved by incorporating blockchain to secure the software transactions, thus introducing the Software-Defined Edge Nodes (SDEN). This will also extend the concept of Fog Computing. A new decentralized architecture for IoT in a smart environment using blockchain for security can be drawn.
E. Supply Chain Management – Smart Supply Contracts
Goods and services are created by manufacturers and are delivered to a retailer (customer) under rules dictated by contractual obligations. Such interactions begin with inquiries from potential customers, which leads to contract negotiation between a supplier and a customer. Once the contracts are signed, the shipping process can begin. This may involve use of a local shipping agency, local port of exit, custom officials, carriers, a distant port of entry, customs services, a distant delivery agent, and finally the customer. At each point, a sequence of messages and acknowledgements is activated culminating in the customer acknowledging receipt of the shipment. Current trading policies on national and international trade also provide details of the process of payment to the supplier. This chain of events is well suited to be adapted to using blockchain technology for the purposes of smooth, verifiable, and secure supply chain management. All documents and events can be recorded and verified at each stage by entering transactions into or querying the appropriate distributed ledger.
References:
[1] Ala Al-Fuqaha et al., “Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications”, IEEE Communications Survey and Tutorials, Vol 17, No.4, Fourth Quarter 2015.
[2] Roberto Minerva, “Towards a Definition of Internet of Things- Revision 1”, IEEE Internet of Things Published 27 May 2015.
[3] Sergey Andreev, “Understanding the IoT Connectivity Landscape: A Contemporary M2M Radio Technology Roadmap” IEEE Communication Magazine, September 2015.
[4] Peter Corcoran, “Internet of Things” IEEE Consumer Electronics Magazine, Jan 2016.
[5] Lawrence T. Yang et al., “Cyber Security in Internet of Things” IEEE Computer, April 2013.
[6] Rodrigo Roman et al., “Securing the Intent of Things” IEEE Computer September 2011.
[7] Satoshi Nakamato “Bitcoin: A peer-to-Peer Electronic Cash System” Available on internet as free article.
[8] Ethereum White Paper at http://github.com/ethereum/wiki/wiki/White-Paper, Accessed on 8th October 2017.
[9] Ahmed Kosba et al. “Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts”, IEEE Symposium on Security and Privacy, 2016, DOI 10.1109/SP.2016.55.
[10] Pantas and Ting, “Blockchain Technology – Beyond Bitcoin” Sutardja Center for Entrepreneurship & Technology, University of California, Berkeley, October 16, 2015. Available on Internet.
[11] Morgan E. Peck, “Do We need a Blockchain” IEEE Spectrum, October 2017, North America Issue.
[12] Konstantinos Christidis et al., “Blockchains and Smart Contract for the Internet of Things”, IEEE Access, DOI 10.1109/ACCESS.2016.25566399, June 3, 2016.
[13] Nir Kshetri, “Can Blockchain Strengthen the Internet of Things”, IEEE IT Pro, July/August 2017.
 Dr. Fatima Hussain
Dr. Fatima Hussain
Dr. Fatima Hussain is currently working as an Adjunct Professor in Ryerson University, Toronto. Prior to this, she was working as an Assistant Professor in University of Guelph, Canada. Ms. Hussain has done her PhD and MASc. in Electrical & Computer Engineering from Ryerson University. She is engaged in various NCSER funded industrial projects such as; Smart Machine Automation, Smart Warehouse, Smart Watch etc. Dr. Hussain has more than 8 years of teaching/ research experience in GTA and overseas. Her research interests include Machine Learning, Internet of Things Networks, and Public Safety. She has dozens of journals and conference papers and an introductory book on "Internet of Things; Building Blocks and Business Models", on her credit. She is serving as an editor and technical lead for IEEE WIE Newsletter, Toronto section.

Dr. Ferworn is a Professor of Computer Science in the Faculty of Science at Ryerson University. Alex has a broad range of research interests related to Computational Public Safety. His award-winning work has been widely publicized in the media. In 2013 he was named the EURAXESS Canadian “Science Slam” champion for his ability to communicate complex ideas to a general audience in compelling ways. “Partners in Research” named him the Canadian “Technology Ambassador” for 2014 for his body of work and his outreach activities.
Javaid Iqbal Zahid
Javaid Iqbal Zahid received his Bachelor of Science in Telecommunication Engineering and Master of Science in Electrical Engineering degree both from University of Engineering and Technology, Lahore, Pakistan. He has over 25 years of experience as in academics and research. He specializes in Signal Processing, Information Theory, Wireless Communication, Information Security, and Analysis of Algorithms. Currently, he is part of Network Centric Applied Research Team (NCART) at Department of Computer Science, Ryerson University, Toronto, Canada. Mr. Javaid is member of IEEE Computer Society, IEEE Communication Society, IEEE Information Theory Society, and Internet Society.
Editor:
 Sinan Hanay
Sinan Hanay
Sinan Hanay received the B.S. in Microelectronics from Sabanci University in 2005, M.S. in Electrical Engineering from TOBB University of Economics and Technology, Turkey in 2007 and Ph.D. in Electrical and Computer Engineering from University of Massachusetts (UMass), Amherst in 2011. During his graduate studies, he worked as a teaching and research assistant at UMass.
He joined Osaka University in 2011 as a post-doctoral researcher. From 2012 to 2016, he worked at Center for Information and Neural Networks (CiNet) of NICT Japan. During that time, he also held visiting researcher and lecturer positions at Osaka University. He is a co-author of a paper which received the best paper award in IEEE International Conference on High Performance Switching and Routing 2011. His research interests include computer networks and machine learning. He is currently an assistant professor at TED University in Turkey.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.



