Why the Future: Internet Use, Users, Service and Terms
By Susan Hyon Parker, IEEE Internet Initiative – Ethics & Policy
IEEE Internet Initiative eNewsletter, November 2017
Discuss this topic on Collabratec:
There has been much knowledge discourse circulated regarding service expansion in private and public sectors regarding the use of technological services and the internet communities that implore its use and users. These discussions have been ideally focused on service and terms and how this will or will not author meeting the needs of global access and adoption as advancements in our society move forward within the digital ecosystem of innovation and productivity. How will these technological changes be embraced? Previously, we initiated discourse expansion of the digital ecosystem for plausible preparatory work and research to be conducted to explore this knowledge and apply new thought processes to meet demands for services and provide opportunities for the unconnected and unbanked. (Hyon Parker, 2016)
Data Source: MySQL.com
“A man who dares to waste one hour of time has not discovered the value of life.” ~ Charles Darwin
In light of technological advancements there are observations made regarding any misgivings in this territorial front. For example, the need to mitigate risk of social engineering actors, privacy ethos, the state and common market wherein there are qualifications of economic interest for effective inclusionary practices. There is also much discussion surrounding protection and security of data with and through the use of machine learning algorithms that possibly make it difficult in mitigating data and financial risks. Here the question arises that asks how is intellectual property and asset forfeiture maintained? It is a thought provoking question most often asked by the user communities for further exploration and consideration among expert groups.
The fear of risk in social engineering by the hackers, identity thieves, disgruntled employees, and recruiters can be perceived as dangerous. The ease of use of account creation for identity theft can cause irreparable damage in physical life. There has been little to no responsibility from internet companies regarding mitigating any physical or psychological damage caused by collateral damage inflicted from online victimization. (Radcliffe, 2017)
Social engineering hackers use several techniques for other forms of security intelligence such as penetration testing, recruitment, threat detection and threat modelling, reputation management, and to remove consolidated data troves. This social engineering hacking provides ease of use to many everyday users through many platforms and the vulnerability of sharing too much information online. Social media platforms are considered honeypots and are a prime target for victimization of communities.
It is important to note that categorically “everyday users” should not be victimized by lack of digital skill or digital assets that would enable them to be productive netizens of the internet community at large. Customer service and technical support professionals need to engage with their public audiences to service customers and provide product support. However, it is critically important that companies provide necessary skills training to their employees to keep customer data private and secure. Security breaches are not only a financial risk but also contribute to customer retention and brand reputation.
For communities that engage with younger audiences, it is critically important to note that content should be delivered appropriately. This is especially important where children and youth are involved as they are our key to a prosperous unity. We look to inclusion champions to partner and engage with these communities to provide this knowledge sharing, mitigate risk, and allow for younger audiences to have the right to choose what is appropriate for their own consumption.
The discourse of division and what it may or may not mean for our internet society in terms of cohesion is currently being researched by “digital divide,” “digital gender divide,” and “net neutrality” initiatives along with their counterparts. However, there is a concern regarding the application of these terms in a physical sense and bridging a gap of skills to accommodate information brokers in delivery of content and services.
The ecological approach by exploring how language makes connections online between subjective experiences and how users construct language into meaning and action will be important for future societal implications. Its use in both intelligent and non-intelligent communities will be decisive for good or ill will.
The internet advocacy conducted in collaboration and conjunction with the Federal Communications Commission (FCC), National Telecommunications and Information Agency (NTIA), and Television White Space Rural Connect should consider the language construct as content delivery is non-neutral whereas spectrum coverage is free of attribute bias that places emphasis on these skill building groups and the associated gap assessments.
The United Kingdom has taken a positive leadership role in this area previously during the Liverpool Audio-Visual Conference held in 2005 in partnership with the European Union’s Television Without Frontier’s Directive regarding the six issues papers and media pluralism. (European Commission Information Society and Media Directorate, 2005)
OFCOM (Office of Communications), the licensing body in the UK has made this free to use, and in the United States the FCC has approved a software application program interface (API) that can be used to gather configuration data without humans for wireless access points. (FCC Spectrum Bridge Database, 2011)
Additionally, HAM radio operators utilize frequencies under gentlemen’s agreement and will need to be considered in the spectrum frequency coverage offered by white space initiatives as they are a secondary user to the FCC and should be included in affordable access initiatives.
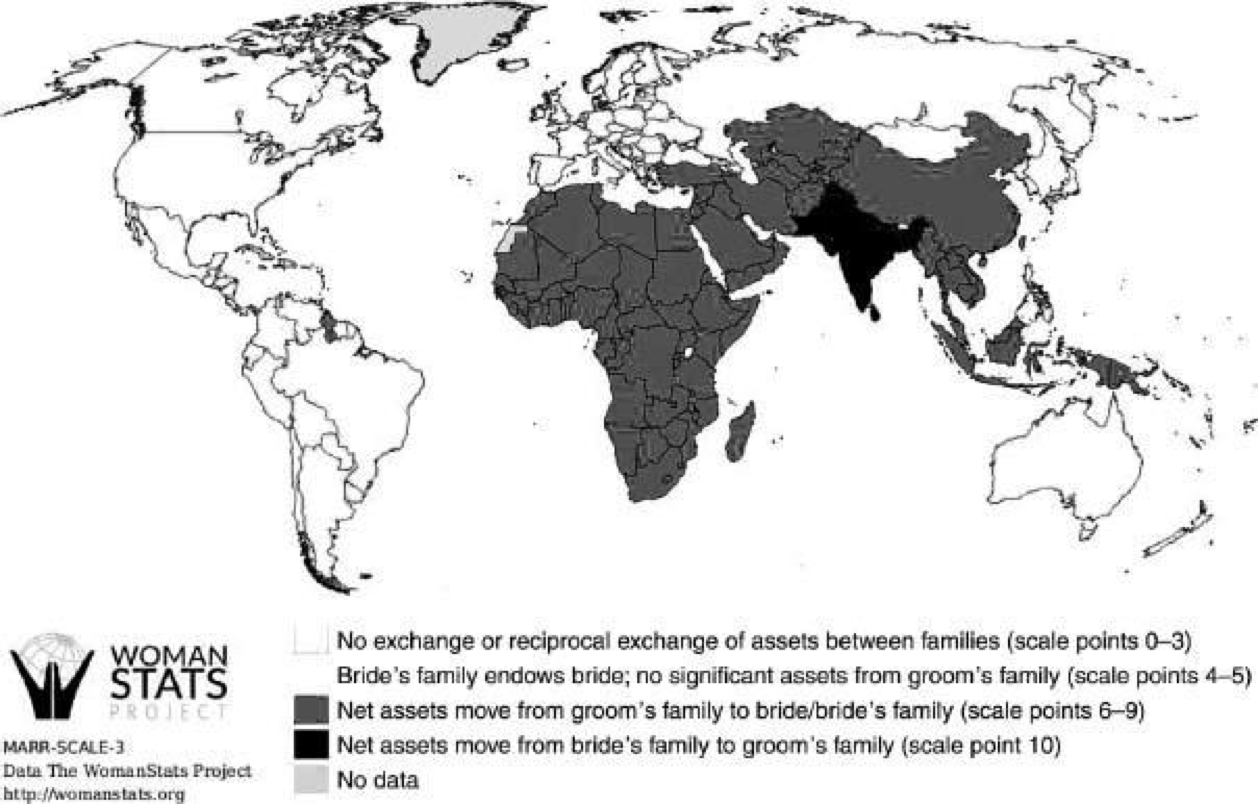
Data Source: (In Plain Sight, Hudson, 2017) [Last Accessed: September 2017]
The ethical, moral, and philosophical considerations provide thoughtful insight into ensuring that these technologies will be used for the betterment, and not the long-term detriment, of the users within these communities. As argued in the recent publication provided by MIT Press, “In Plain Sight” (Massachusetts Institute of Technology Press, 2017) provides opportunity for discourse in the neglected linkage between ethical financial transactions where cultures may not be known or understood.
In a forward-thinking leadership role, the European Commission has taken guidance on Article 345 which supports agnosticism and Article 36 of the charter of Fundamental Rights which provides that the Union recognize and respect access to the services of general economic interest as provided for in national laws and practice.
The use of General Data Protection Regulation (GDPR) and network based conflict of politically motivated attacks toward the abuse of users should be considered when sharing data with internet companies that don’t have a direct relationship with the user or its community. This is especially important for those internet companies who are championing inclusion agendas. (The European Commission, 2000) and (The European Commission, 2017)
The global landscape of connectivity, inclusion, digital skills, entrepreneurship, and affordability moves forward—celebrating essential humanity that encourages a future without scrutiny and promotes continued cooperation with the laws of nature.
References:
[1] European Commission Information Society and Media Directorate. (2005, July).
[2] Centre for Global Communication Studies. Retrieved from Annenberg School for Communication University of Pennsylvania: http://global.asc.upenn.edu/fileLibrary/PDFs/ispa_advertising.pdf [September 2017]
[3] Hudson, V. M. (2017, June). Woman Stats Project. Retrieved from Woman Stats Project: http://www.womanstats.org/index.htm
[4] Hyon Parker, S. (2016, September). IEEE Internet Initiative. Retrieved from IEEE Internet Policy Letters: https://internetinitiative.ieee.org/newsletter/september-2016/
[5] Radcliffe, J. (2017, May). Social Engineering Training. Retrieved from Jenny Radcliffe: http://jennyradcliffe.com/security-and-social-engineering/
[6] Massachusetts Institute of Technology Press. (2017). In Plain Sight: The Neglected Linkage between Brideprice and Violent Conflict. International Security Vol. 42 No. 1 (Summer).
[7] The EU General Data Protection. (2017). Retrieved from EU GDPR: http://www.eugdpr.org/
[8] The European Commission. (2000, December). Charter of Fundamental Rights of the European Union. Retrieved from Official Journal of the European Communities: http://www.europarl.europa.eu/charter/pdf/text_en.pdf
[9] The European Commission. (2017). EU Charter of Fundamental Rights. Retrieved from European Union Agency of Fundamental Rights: http://fra.europa.eu/en/charterpedia/article/36-access-services-general-economic-interest
 Susan Hyon Parker
Susan Hyon Parker
Susan Hyon Parker received her B.S. in Computer Science from Robert Morris University. She received her engineering education jointly through Carnegie Mellon University and Massachusetts Institute of Technology. She is currently pursuing her PhD in Nanotechnology. She was a visiting student at University of Oxford and is presently a UK Engineering STEM Learning ambassador. She is Founder of NanoSchool.eu™, which places emphasis on opportunities to work on authentic research projects alongside academic and industrial scientists as well as engineers using distinctive design approaches. She is participating in Toulouse ESOF 2018 Science Forum and is member of the Nanotechnologies Industry Association.
She has been an instructor with the Carnegie Mellon Open Learning Initiative since its inception in 2001. She is an active member of the IEEE Internet Initiative, IEEE Nanotechnology, IEEE Cybersecurity, IEEE Smart Grid Power & Energy Society. She has been a contributor to the IEEE ETAP Forum and Conferences and has been reviewing papers for the National Academy of Engineering - Engineer Girl Essay Contest.
Her research interests include Sensor and Ad hoc networks, Robotics, Artificial Intelligence, Neuroscience, Cyber Physical Systems, Vehicular Communications, Graphene, Renewable Energy, IoT and Future Internet Autonomous Systems and Propulsion and Aerospace Systems.
Editor:
 Dr. Syed Hassan Ahmed (S’13, M’17)
Dr. Syed Hassan Ahmed (S’13, M’17)
Syed Hassan Ahmed completed his B.S in Computer Science from Kohat University of Science & Technology (KUST), Pakistan and Masters combined Ph.D. Degree from School of Computer Science and Engineering (SCSE), Kyungpook National University (KNU), Republic of Korea. In summer 2015, he was also a visiting researcher at the Georgia Tech, Atlanta, USA. Collectively, Dr. Hassan authored/co-authored over 100 international publications including Journal articles, Conference Proceedings, Book Chapters, and 02 books. From the year 2014 to 2016, he consequently won the Research Contribution awards by SCSE at KNU, Korea. In 2016, his work on robust content retrieval in future vehicular networks lead him to win the Qualcomm Innovation Award at KNU, Korea. Currently, Dr. Hassan is a Post-Doctoral Fellow in the Department of Electrical and Computer Engineering, University of Central Florida, Orlando, FL, USA. His research interests include Sensor and Ad hoc Networks, Cyber-Physical Systems, Vehicular Communications and Future Internet.
Dr. Hassan is an IEEE and ACM member, serving as a TPC Member or Reviewer in 60+ International Conferences and Workshops including IEEE Globecom, IEEE ICC, IEEE CCNC, IEEE ICNC, IEEE VTC, IEEE INFOCOM, ACM CoNEXT, ACM SAC, and much more. Furthermore, he has been reviewing papers for 30+ International Journals including IEEE Wireless Communications Magazine, IEEE Networks Magazine, IEEE Communications Magazine, IEEE Communications Letters, IEEE Sensors Letters, IEEE Transactions on Industrial Informatics | Vehicular Technologies | Intelligent Transportation Systems | Big Data | Mobile Computing, Elsevier Computer Communications, and Computer Networks.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.



