Blockchain: Vision and Challenges
By Gurkan Caglar and Y. Sinan Hanay
Department of Computer Engineering, TED University, Turkey
IEEE Internet Initiative eNewsletter, September 2017
Discuss this topic on Collabratec:
Blockchain is a new and advancing technology. Even though it started with Bitcoin and is used widely in crypto-currencies, it now has non-financial uses in many areas and applications. The true limits of blockchain are still unknown and developers and pioneers are in uncharted territory. Arguably the most important promise of blockchain is the obviation of need for a central authority in multi-party applications, especially where users do not inherently trust each other.
What is blockchain?
Blockchain is a structure that consists of blocks. Each block contains a nonce, timestamp, the hash of the previous block and transaction (new data in non-financial applications). The blockchain works as follows. Transaction requests constantly arrive, but it is up to the majority of users to accept those requests. After a transaction is accepted, the hash of the previous block, timestamp and nonce is added in to the new block. Since every block contains the previous block’s hash value, this system is secure because if one block’s contents change, hash values would not add up.
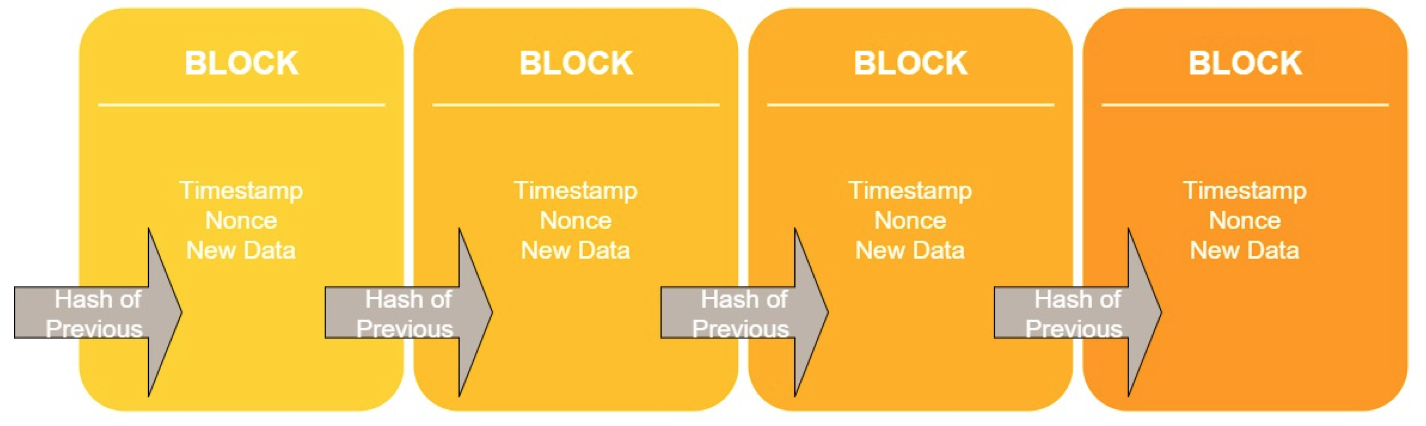
Figure 1: The stages
Blockchain consists of every transaction ever made so it is a complete ledger. This ledger system offers many benefits. Your data is always secure; it is quite difficult to tamper with it as you need to have the information from the genesis block and every block created after that initial point to be present to get the right hash value. The system also eliminates the need for third parties, and with them being out of the picture, the data security is not a question anymore.
The most popular example of blockchain is crypto-currencies; however, there are other domains which benefit from blockchain. Details about these applications can be found in[1, 2, 3]. The following list briefly summarizes areas and specific applications that leverage blockchain:
- Music industry: A company called Dot Blockchain Media works on a project that can determine music royalties and manage music ownership.
- Agricultural industry: CBH group and AgriDigital are now working on a project to provide real-time settlement for physical grain deliveries on a private Ethereum network.
- E-Democracy: Voting systems are more secure because every vote is recorded and they are immutable with the blockchain’s structure. This system was first used in a Danish political party’s internal elections.
- Decentralized storage: StorJ is a decentralized storage system which employs blockchain, eliminating the need for a third party to store data because this system works peer-to-peer on personal computers. Since there is no third party, every piece of data that resides in a peer’s computer is encrypted with AES256 data and is secure with a symmetric key.
- Insurance: Everledger started with diamonds and it creates a database from blockchain to hold parameters about the given diamond. The company can identify where the diamond comes from, where it has gone, who owns it and where it is now. They advanced their business model from diamonds to other high-value objects.
- Anti-counterfeit: Blockverify is a company which can identify counterfeit items thanks to companies that create a register of their own products with blockchain as a data structure. Blockverify can detect counterfeit, diverted, and stolen products. The company has a big pool of items ranging from pharmaceuticals and luxury items to electronics and diamonds.
- Decentralized Domain Name System (DNS) and Transport Layer Security (TLS): A company named Namecoin implemented first decentralized DNS and works on decentralized TLS (HTTPS) certificate validation. Its aim is to eliminate the need of a government agency or corporations over DNS.
- Decentralized Internet of Things (IoT): IBM, Samsung and Filament are working to find a way to reliably store the communication of smart devices in IoT.
With many companies focused on blockchain, there are still some problems that need to be addressed. Some of these problems and their proposed solutions are listed below:
- Privacy: Blockchain is available and trusted in the sense of the transaction, but these transactions are open and can be seen by anyone since it is P2P. In a scenario for an auction, a framework called Hawk ensures that transactions are encrypted and frozen until all the bids reach a minimally trusted party called the manager with the help of zero knowledge proof[4]. With this system only a manager knows the identities of the bidders, and this causes another problem because the manager could share this info.
- Scalability: A group from Cornell University claims that blockchain derived from Bitcoin has scalability limits, and it causes a trade-off problem between throughput and latency. The group suggests a new Byzantine fault-tolerant blockchain protocol called Bitcoin-NG and it can withstand extreme churn[5].
- Data security: We have talked about blockchain data storage while mentioning decentralized data storage, but this is about permissions. Some authors talk about the problem uncontrollable permission gave to applications[6]. They propose a blockchain that accepts two new types of transaction: Taccess and Tdata. Initially giving access and uploading data, both the service and user can now query the data, but the proposed system states that users can change the access privileges and protect their data whenever they want.
- Block withholding: This was an important attack on blockchain[7] proposing systems that prevent miners from knowing if they have the partial or the full proof of work by making some minor changes to Bitcoin protocol.
Many businesses embrace blockchain in various domains because of its great flexibility. It provides security with less hassle as it eliminates the need of third parties. The decentralized mechanism of blockchain resembles the end-to-end principle design of the internet, which was established five decades ago.
References:
[1] S. Underwood, “Blockchain beyond bitcoin,” Commun. ACM, vol. 59, no. 11, pp. 15–17, 2016.
[2] M. Nofer, P. Gomber, O. Hinz, and D. Schiereck, “Blockchain,” Bus. Inf. Syst. Eng., vol. 59, no. 3, pp. 183–187, 2017.
[3] M. Lansiti and K. R. Lakhani, “The truth about blockchain,” Harvard Business Review, no. January-February. 2017.
[4] A. Kosba, A. Miller, E. Shi, Z. Wen, and C. Papamanthou, “Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts,” in 2016 IEEE Symposium on Security and Privacy (SP), 2016, pp. 839–858.
[5] I. Eyal, A. E. Gencer, E. G. Sirer, and R. van Renesse, “Bitcoin-NG: A Scalable Blockchain Protocol,” 13th USENIX Symp. Networked Syst. Des. Implement. (NSDI 16), pp. 45–59, 2016.
[6] G. Zyskind, O. Nathan, and A. S. Pentland, “Decentralizing privacy: Using blockchain to protect personal data,” in Proceedings - IEEE Security and Privacy Workshops, 2015, pp. 180–184.
[7] S. Bag, S. Ruj, and K. Sakurai, “Bitcoin Block Withholding Attack: Analysis and Mitigation,” IEEE Trans. Inf. Forensics Secur., vol. 12, no. 8, pp. 1967–1978, 2017.
 Gurkan Caglar
Gurkan Caglar
Gurkan Caglar graduated from Ankara Gazi Anadolu High School in 2010. He is now an undergraduate student in Computer Engineering at TED University. He is eager to make research about computer networks, computer graphics, and image processing.
 Y. Sinan Hanay
Y. Sinan Hanay
Dr. Y. Sinan Hanay received the B.S. in Microelectronics from Sabanci University in 2005, M.S. in Electrical Engineering from TOBB University of Economics and Technology, Turkey in 2007 and Ph.D. in Electrical and Computer Engineering from University of Massachusetts (UMass), Amherst in 2011. During his graduate studies, he worked as a teaching and research assistant at UMass.
He joined Osaka University in 2011 as a post-doctoral researcher. From 2012 to 2016, he worked at Center for Information and Neural Networks (CiNet) of NICT Japan. During that time, he also held visiting researcher and lecturer positions at Osaka University. He is a co-author of a paper which received the best paper award in IEEE International Conference on High-Performance Switching and Routing 2011. His research interests include computer networks and machine learning. He is currently an assistant professor at TED University in Turkey.
Editor:
 Shakil Muhammad
Shakil Muhammad
Shakil Muhammad received his Bachelor of Computer Engineering degree from Bahria University, Karachi Campus, in 2005. He received his M.S in Information and Telecommunication Technology from Korea Advanced Institute of Science and Technology (KAIST), Daejeon, South Korea, in 2012. He has worked for National Engineering & Scientific Commission (NESCOM) as Deputy Project Director for 10 and half years. He possesses several network system and security certifications /training such as Red Hat Certified Engineer (RHCE), Certified Ethical Hacker (CEH), Certified Information System Auditor (CISA); DNS Sec etc. He is currently working toward the Ph.D. degree in the Department of Information and Telecommunication Technology, KAIST. His research interests include the areas of Software Defined Networking, Network Function Virtualization, Internet of Things, Clouds and Security & Privacy issues. He has published several national and international conferences papers.
Article Contributions Welcomed
If you wish to have an internet policy related article considered for publication, please contact the Managing Editor of Technology Policy and Ethics IEEE Future Directions Newsletter.
Past Issues
IEEE Internet Policy Newsletter Editorial Board
Dr. Ali Kashif Bashir, Interim Editor-in- Chief
Dr. Syed Hassan Ahmed
Dr. Mudassar Ahmad
Dr. Onur Alparslan
Dr. Muhammad Bilal
Dr. Syed Ahmad Chan Bukhari
Dr. Ankur Chattopadhyay
Dr. Junaid Chaudhry
Dr. Waleed Ejaz
Dr. Yasir Faheem
Dr. Prasun Ghosal
Dr. Tahir Hameed
Dr. Y. Sinan Hanay
Dr. Shagufta Henna
Dr. Fatima Hussain
Dr. Rasheed Hussain
Dr. Saman Iftikhar
Dr. Stephan Jones
Dr. Mohammad Saud Khan
Olga Kiconco
Dr. Jay Ramesh Merja
Dr. Mubashir Husain Rehmani
Dr. Hafiz Maher Ali Zeeshan
About: This newsletter features technical, policy, social, governmental, but not political commentary related to the internet. Its contents reflect the viewpoints of the authors and do not necessarily reflect the positions and views of IEEE. It is published by the IEEE Internet Initiative to enhance knowledge and promote discussion of the issues addressed.



